🚨 SCAM ALERT: “This Will Go Public” Email – Here’s What You Need to Know
Cybercriminals are getting sneakier, and this latest scam is a perfect example. If you’ve received an email titled “This Will Go Public” or “Note to Self” and it appears to come from your own email address, don’t panic. You’re not alone, and this is a classic email spoofing scam meant to scare you into action.
🕵️♂️ What Happened?
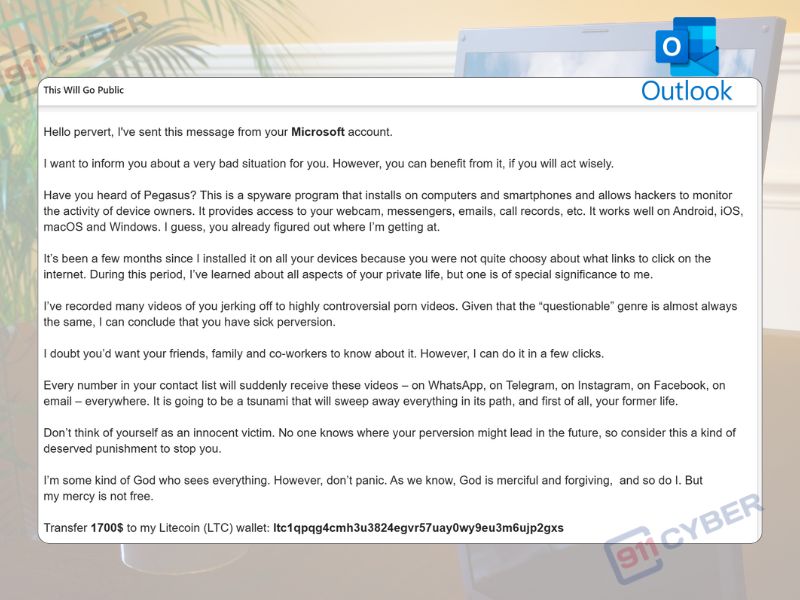
The scam email is designed to appear as if it’s sent from your own Hotmail account, using fear tactics like threats of exposure or “public leaks” to manipulate you. But in reality, this message is:
- Not sent by you
- Not from Microsoft or Outlook
- Part of a widespread phishing and extortion scam
Let’s break down how this scam works using technical evidence from the email headers.
🔍 Technical Breakdown: Clues in the Header
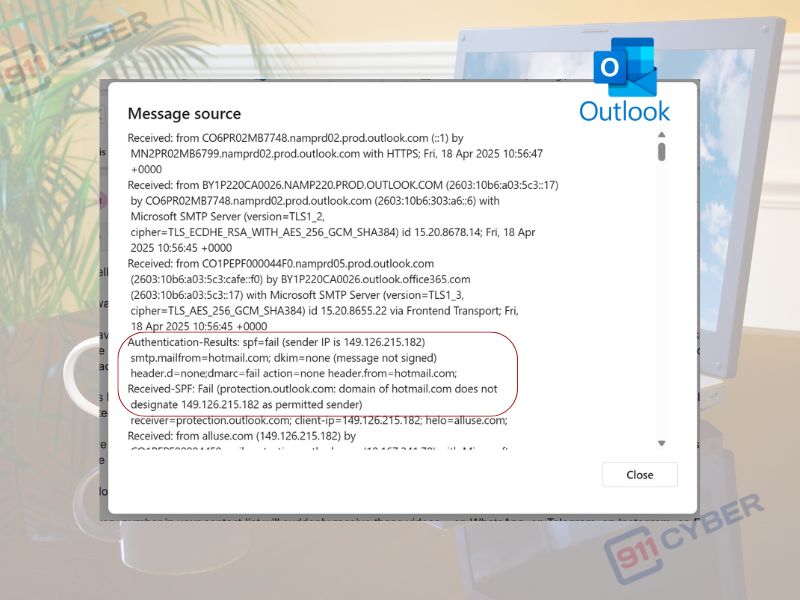
Here are key red flags found in the email headers:
1. Sender IP Mismatch
Received-SPF: Fail (protection.outlook.com: domain of hotmail.com
does not designate 149.126.215.182 as permitted sender)
✅ Hotmail’s SPF (Sender Policy Framework) says this IP address is not authorized to send on behalf of hotmail.com. That’s a big sign of spoofing.
2. DKIM and DMARC Fail
dkim=none (message not signed dmarc=fail action=none header.from=hotmail.com;
✅ The message lacks a valid DKIM signature and fails DMARC checks, which are email authentication methods used to prevent domain spoofing.
3. Suspicious Origin Server
Received: from alluse.com (149.126.215.182)
✅ Despite appearing to be from Hotmail, it was actually sent from a suspicious domain (alluse.com) and IP address located outside of Microsoft’s infrastructure.
4. Self-Spoofed ‘From’ Address
From: "myemail@hotmail.com" <myemail@hotmail.com> To: <myemail@hotmail.com>
✅ The scammer is trying to trick you by making it look like you emailed yourself. That’s classic social engineering.
😱 What Does the Email Say?
While the content may vary, it usually includes:
- Blackmail threats
- Claims they hacked your account or webcam
- Demands for cryptocurrency or personal data
- Urgency (“This will go public unless…”)
It’s a fake threat. Scammers use fear to push people into sending money or giving up control.
🔒 How to Protect Yourself
- Don’t respond. Any reply confirms your address is active.
- Don’t click links or download anything.
- Check your account security:
- Change your password if reused or weak.
- Enable two-factor authentication.
- Mark as phishing in Outlook or your email provider.
- Report the email to Microsoft: Report phishing
Get Help: Contact one of our cybersecurity experts for guidance.
Final Thoughts
This scam is a good reminder: just because an email looks like it came from you doesn’t mean it did. Email protocols like SPF, DKIM, and DMARC exist to catch exactly this kind of forgery—but scammers hope you don’t know how to check.
Stay informed. Stay alert. Don’t fall for fear tactics.
Get Help
Legal Briefs Turned Breach Fodder
Spot and Avoid EZPass Toll Payment Scams
Do You Feel Like Your Identity Has Been Stolen?
Beware of EBT Scam Texts
Lost Access to Social Media Accounts?








